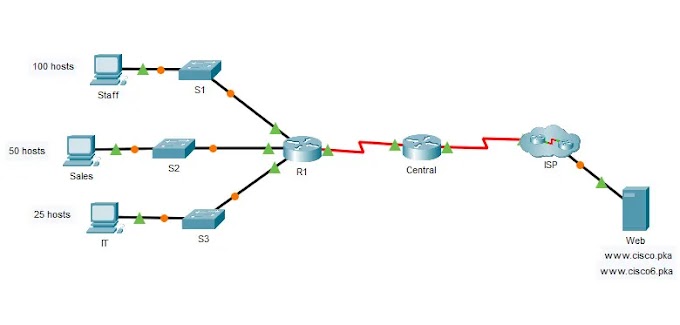
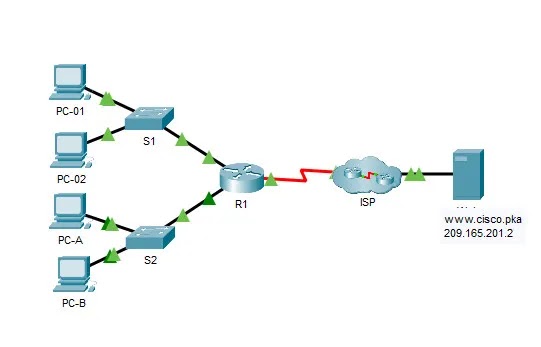
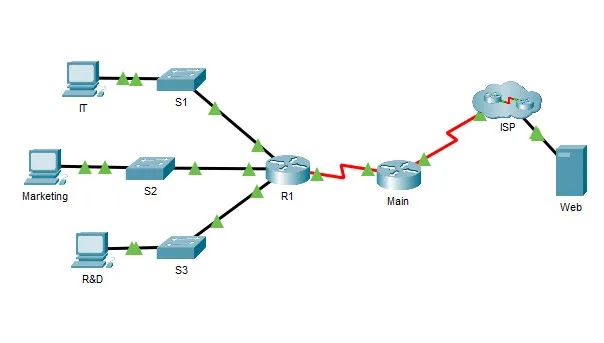
Passing the 300-715 Implementing and Configuring Cisco Identity Services Engine (SISE) test using DumpsBase's updated 300-715 pdf dumps must be a solid solution. All in all, the 300-715 dumps V14.02 come with 189 practice exam questions and answers, providing you with all the necessary study materials and top-level 300-715 practice questions and answers to pass the 300-715 Implementing and Configuring Cisco Identity Services Engine Exam on your first attempt.
* Please Don't Spam Here. All the Comments are Reviewed by Admin.
Popular Posts
Labels
Most Recent
4/sidebar/recent
Header Ads Widget
Footer Copyright
Design by - Blogger Templates | Distributed by Free Blogger Templates

.jpg)